14 Which of the Following Are Breach Prevention Best Practices
3 2015 Definitions. Out of the box AWS offers.

Amulet Winery Investors Sue Tuck And Boo Beckstoffer Alleging Breach Napa Valley Wineries Meadowood Napa Valley Winery
The following best practices may help.

. HIPAA and Breach Prevention. 14 which of the following are breach prevention best practices. Which of the following are breach prevention best practicesAccess only the minimum amount of PHIpersonally identifiable information PII necessaryLogoff or lock your workstation when it is unattendedPromptly retrieve documents containing PHIPHI from the printerAll of this above.
Best Practices for Enterprise Cloud Security. Protects electronic PHI ePHI c. Are breach prevention best practices.
Breach prevention strategies TheftLoss. You might also consider the following recommendations. Conduct a Risk Assessment Before any solution is implemented it is important to know.
Logoff or lock your workstation when it is unattended. Best Practices for Incident Response Plans The First 24 Hours Following a Breach Questions Reputation. Best practices for incident response plans the first 24 hours following a breach questions reputation.
All of the above answer a. Invest in up-to-date data loss prevention DLP technology. Established a national set of standards for the protection of PHI that is created received maintained or transmitted in electronic media by a HIPAA covered entity CE or business associate BA b.
What are breach prevention best practices. 2 Which of the following are breach prevention best practices. Discuss best practices for preventing breaches.
S3 Breach Prevention. Access only the minimum amount of PHIpersonally identifiable information PII necessary. Perform suspicious email training exercises to help employees identify potentially nefarious emails.
13 Best Practices You Should Implement. All of the above You can help prevent a breach by accessing only the minimum amount of PHIPII necessary and by promptly retrieving documents containing PHIPII from the printer. Remediation Accessed N PHI transmitted orally PHI on paper PHI transmitted electronically correct All of the above-----11 Which of the following are breach prevention best practices.
Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly retrieve documents containing PHIPHI from the printer All of this above correct 3 The minimum necessary standard. Discuss best practices for preventing breaches. Access only the minimum amount of PHIpersonally identifiable information PII necessary.
10 The HIPAA Security Rule applies to which of the following. You should always logoff or lock your workstation when it. Addresses three types of safeguards - administrative technical and physical.
When a data breach occurs involving a cloud service the impulsive reaction is to denounce using the cloud at least for sensitive information. 3 2015 Definitions. Data Breach Prevention.
10 Best Practices for Data Breach Prevention by Jason Coggins Updated On - 06152020 Data Security Almost 15 billion data records have been lost or stolen since 2013 an issue that affects North America disproportionately more than other parts of the world. Regularly monitor networks and databases for unusual traffic. Notice to the individual no later than 60 days following discovery of the breach via first-class mail or email Notice must include.
Breach prevention strategies TheftLoss. Train employees on data security practices and awareness. Best Practices in Breach Prevention Develop appropriate security measures Monitor compliance with required measures Comply with reporting requirements W.
Strong passwords are considered over eight characters in length and made up of both upper and lowercase letters numbers and symbols. Access only the minimum amount of PHIpersonally identifiable information PII necessary Logoff or lock your workstation when it is unattended Promptly. 2 Data Breach Landscape Data breaches cost companies an average of 221 per compromised record.
Since cloud security is not widely understood it may be difficult to delineate it in the context of more general information security.

Businessman Login With Fingerprint Scanning Technology Fingerprint Digital Lock Fingerprint Lock

The Five Most Common Attack Patterns Behind Today S Data Breaches Tripwire Cyber Security Tech Apps

The Job Of Dataprotection Is Getting Tougher Every Day And Minor Mistakes Can Cost Any Organization Thousands Of Dollars Data Loss Prevention Data Loss Data
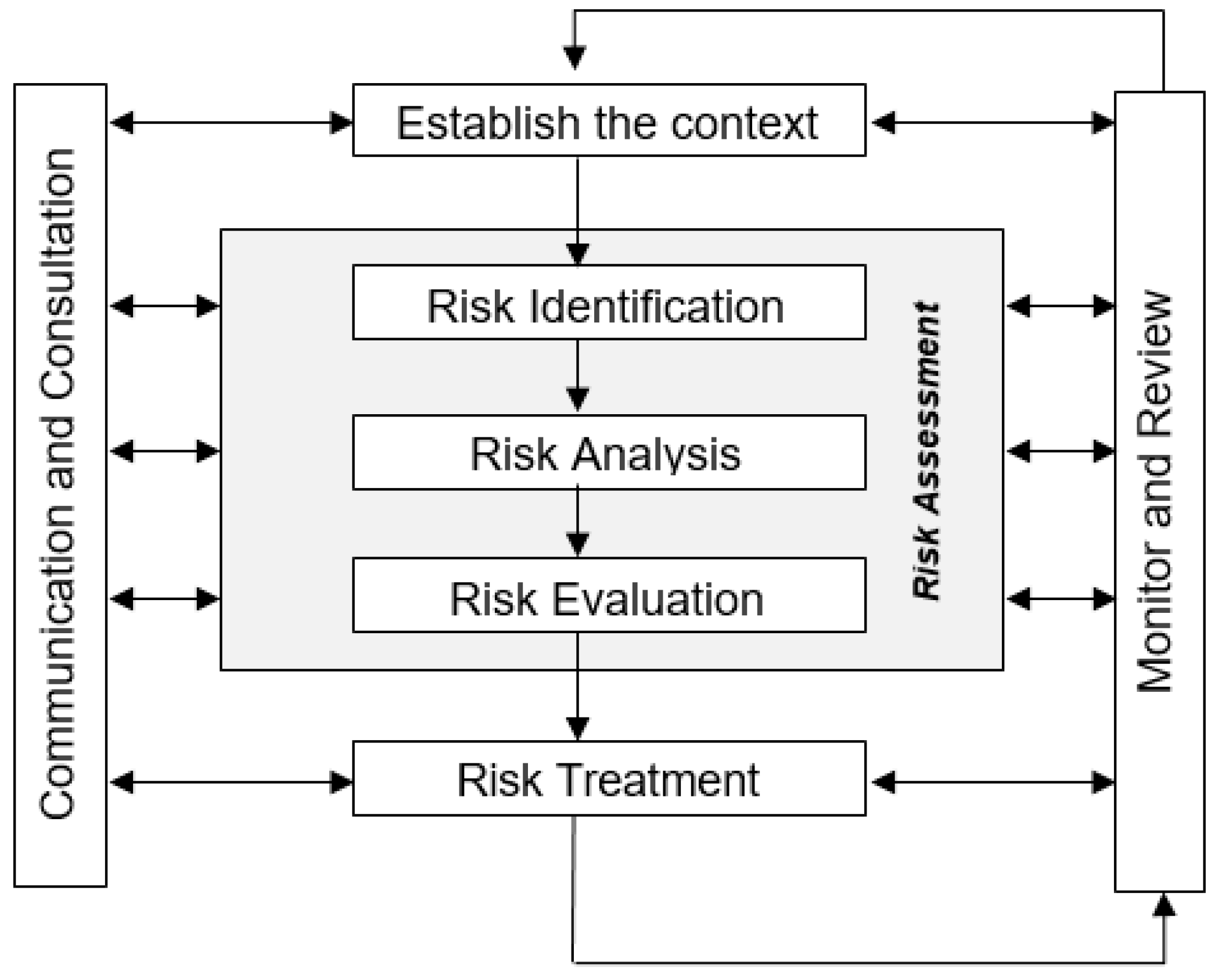
Jrfm Free Full Text How Can Enterprise Risk Management Help In Evaluating The Operational Risks For A Telecommunications Company Html

Guidesforbackup On Twitter Software Security Wordpress Security Cyber Security
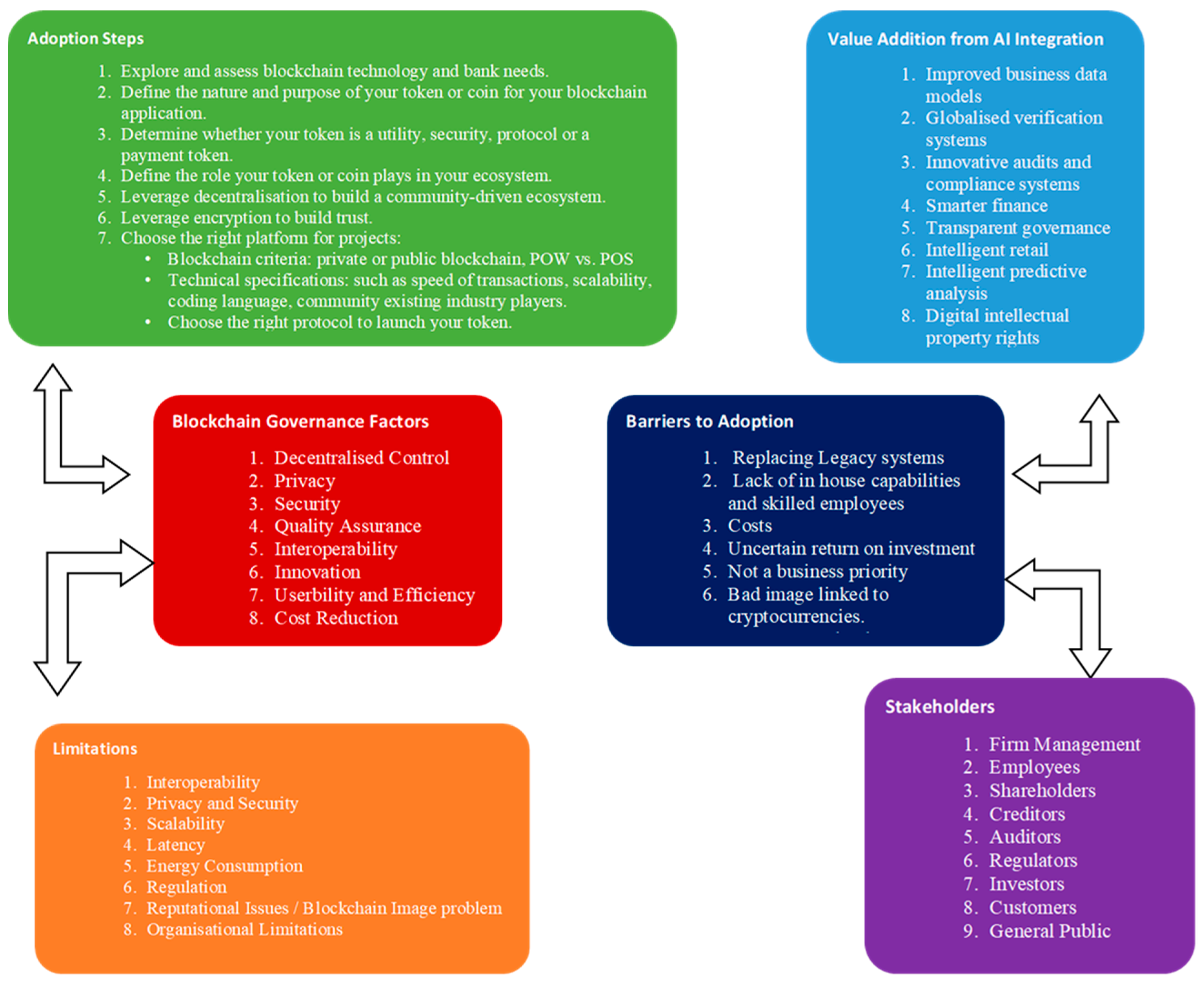
Jrfm Free Full Text Fantastic Beasts Blockchain Based Banking Html

Healthcare Information Security 5 Ways To Maintain In 2022

A Guide To Cyber Security For Law Firms In 2021 Cyber Security Security Solutions Security

What Is The Need Of Ip Addresses Restriction In Enterprises Understand The Importance Of Implementing Ip Add In 2021 Cloud Data Internet Protocol Address Ip Address

Best Truck Driving Jobs Images On Pinterest Driving Truck Driving Jobs Trucks Truck Driver Jobs

Risk Management B2holding Annual Report 2020
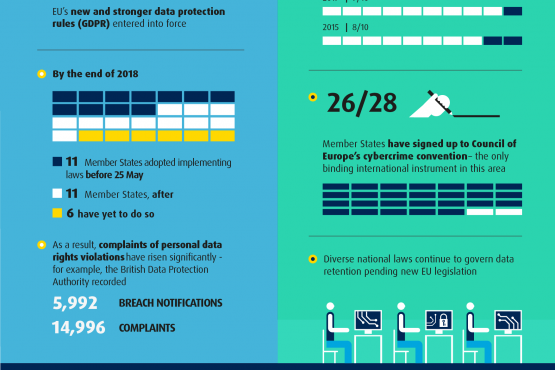
Data Protection Privacy And New Technologies European Union Agency For Fundamental Rights

How Not To Greet A Dog 11 X 14 Kid Friendly Poster Zazzle Com In 2022 Dog Body Language Dog Biting Dog Language

Microsoft Announces Upcoming Email Encryption For Office 365 The Tech Journal Data Folders Office 365 Microsoft

4 Practical Techniques And Countermeasures To Battle Ransomware Carbon Black Prevention Cyber Security Optimization
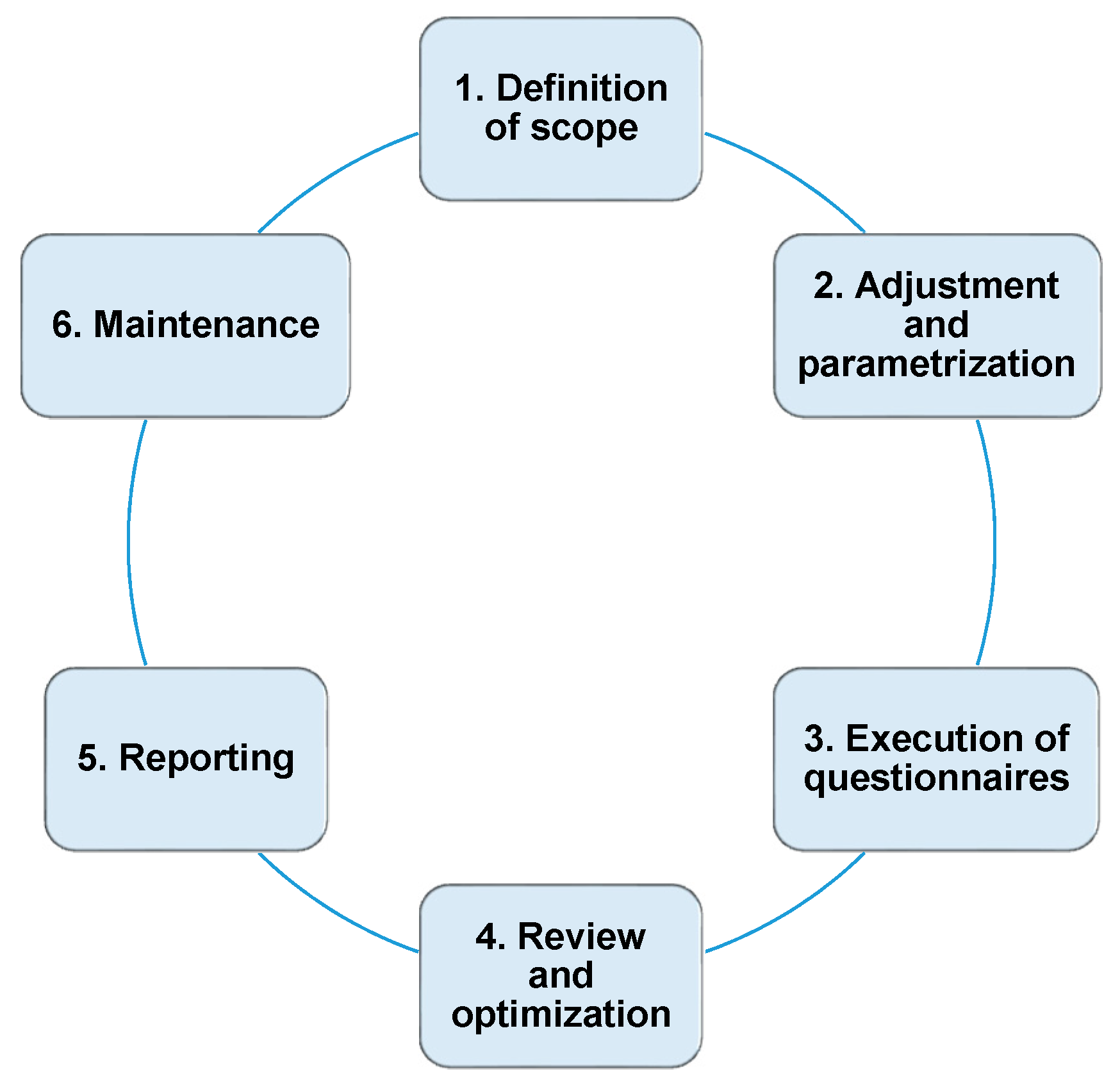
Jrfm Free Full Text How Can Enterprise Risk Management Help In Evaluating The Operational Risks For A Telecommunications Company Html

12 Ways To Protect Your Business From A Ransomware Attack Infographic Cybersecurity Infographic Infographic Cyber Security
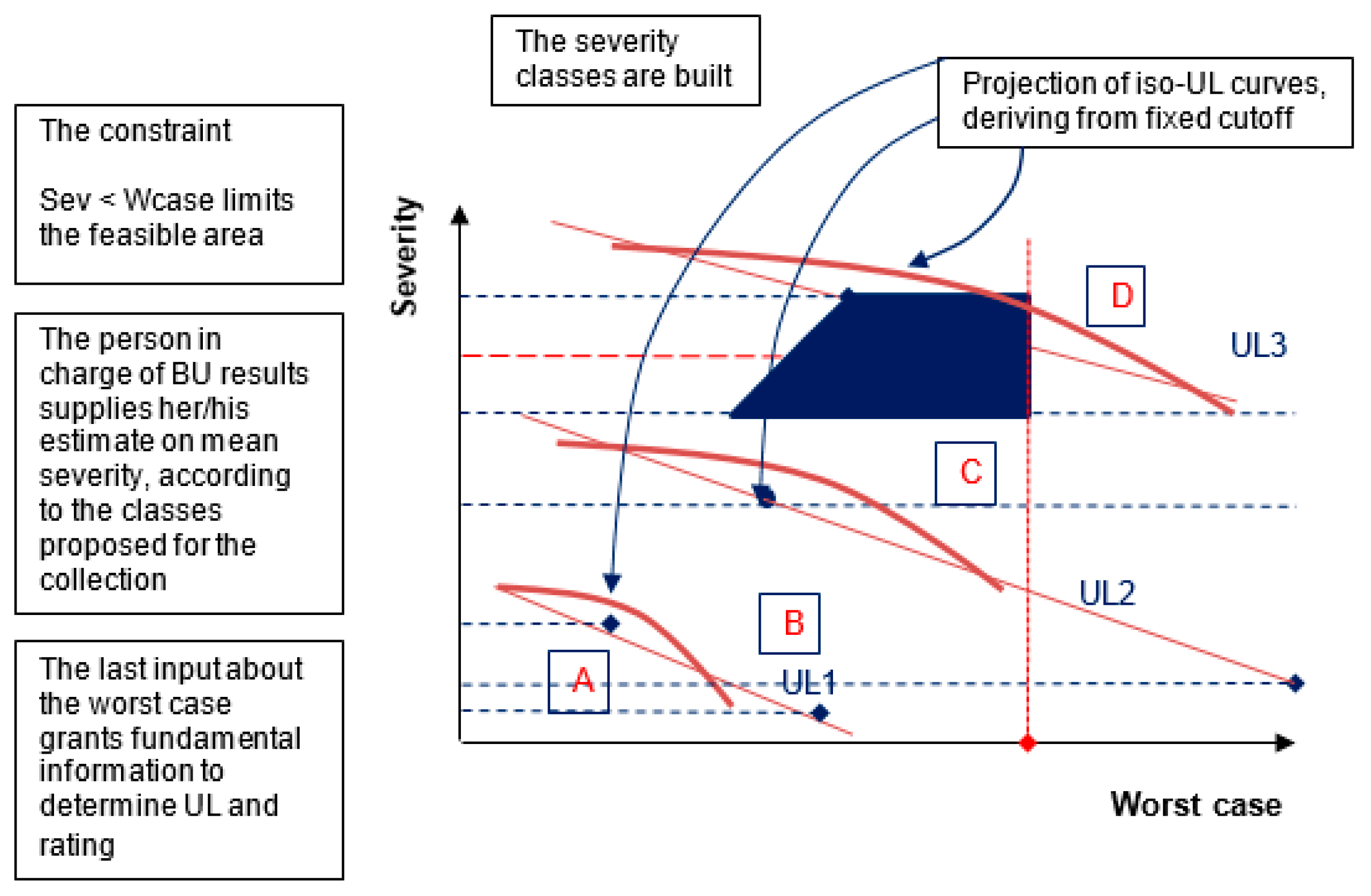
Jrfm Free Full Text How Can Enterprise Risk Management Help In Evaluating The Operational Risks For A Telecommunications Company Html
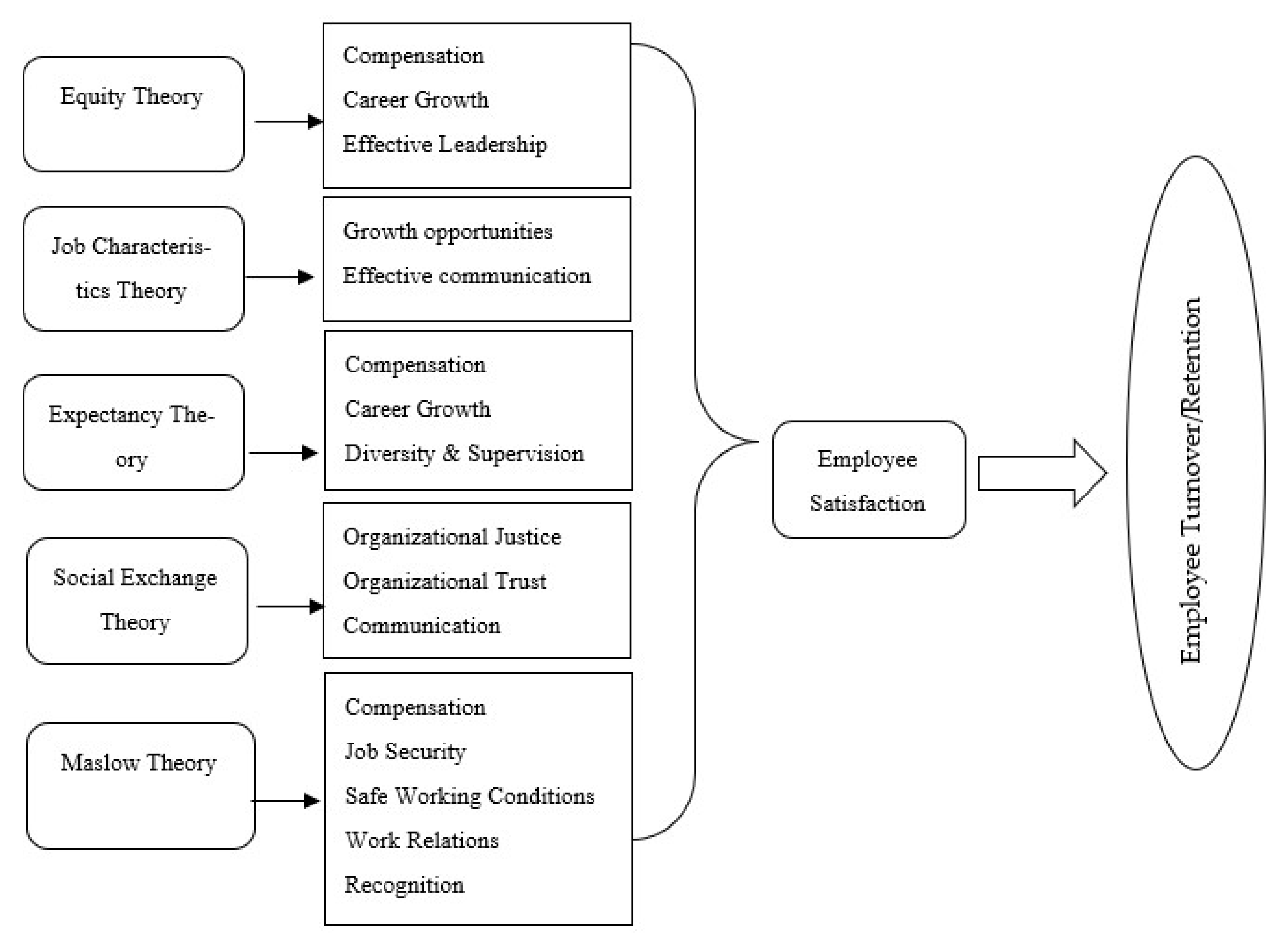
Sustainability Free Full Text Challenges And Strategies For Employee Retention In The Hospitality Industry A Review Html
Comments
Post a Comment